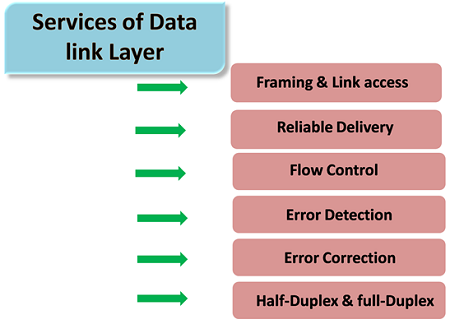
Briefly Describe The Services Provided By The Data Link Layer
A method is provided for acquiring and transmitting biometric data eg vital signs of a user where the data is analyzed to determine whether the user is suffering from a viral infection such as COVID-19. Manuals from the site are more up-to-date than manuals derived from the Yocto Project released TAR files.
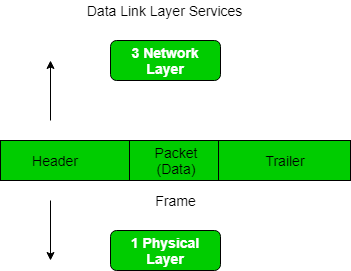
Framing In Data Link Layer Geeksforgeeks
C1 Basic Viewpoints in the ArchiMate Language.
Briefly describe the services provided by the data link layer. They also provide services based on hardware features of a device such as the GPS compass accelerometer and gyroscope. Data communication and terminal equipment 17. PyLoris can utilize SOCKS proxies and SSL connections and can target protocols such as HTTP FTP SMTP IMAP and Telnet. Or data terminal equipment DTE such as a digital telephone handset a printer or a host computer. We would like to show you a description here but the site wont allow us. Assuming you want to send an e-mail message to someone in Italy we will examine the layers from the bottom up -- beginning with Ethernet physicaldata link layers.
Frames are defined at Layer 2 or the Data Link Layer of the Open Systems Interconnection OSI seven-layer network model. It is used to define how that information will be sent and to structure the development of standards for transferring. PyLoris is a scriptable tool for testing a servers vulnerability to connection exhaustion denial of service DoS attacks. We strive to ensure that every paper is crafted with getting you the highest grade in mind. This cloud model is composed of five. All our customer data is encrypted.
Article 82 of Regulation EC No 12722008 shall apply. It uses the functions provided by the connectivity layer and calls directly the interfaces made available by the fabric layer. We consider our clients security and privacy very serious. In data communication a physical network node may either be data communication equipment DCE such as a modem hub bridge or switch. Request a specific writer choose an academic writer from the dropdown list in the orders form optional for returning customers. In the next chapter we describe the organisation and the operation of Local Area Networks.
During its development versions of it were known as the Department of Defense DoD model because. By far the most. Second-generation AirPods Pro will have lossless audio support and a charging case that can emit a sound for location tracking purposes Apples second-generation AirPods Pro will feature support for Lossless audio and a charging case that can emit a sound for location tracking purposes according to Apple analyst Ming-Chi Kuo. Our services are very confidential. The method includes using a pulse oximeter to acquire at least pulse and blood oxygen saturation percentage which is transmitted wirelessly to a smartphone. Our records are carefully stored and protected thus cannot be accessed by unauthorized persons.
A viewpoint in the ArchiMate language is a selection of a relevant subset of the ArchiMate elements and their relationships. The Internet protocol suite commonly known as TCPIP is the set of communications protocols used in the Internet and similar computer networksThe current foundational protocols in the suite are the Transmission Control Protocol TCP and the Internet Protocol IP. Due to its learning capabilities from data DL technology originated from artificial neural network ANN has become a hot topic in the context of computing and is widely. The most basic type of viewpoint is a simple selection of a relevant subset of the ArchiMate concepts. Choose the Writers Samples option study 3 randomly-provided pages from orders that have been written by the assigned writer. Ethernet PhysicalData Link Layers The physical layer of the network focuses on hardware elements such as cables repeaters and network interface cards.
To enable proper control measures to be taken all relevant information on the substance or. If the network in question is a local area network LAN or wide area network WAN every LAN or WAN node. This section of the safety data sheet shall describe the empirical data relating to the substance or mixture if relevant. Get 247 customer support help when you place a homework help service order with us. Transferring of files disturbing the results to the user is also done in this layer. This version of the Yocto Project Mega-Manual is for the 31 release of the Yocto Project.
A protocol agnostic application layer denial of service attack. The seven-layer model was developed to organize the kinds of information sent between computers. For example this layer will offer functions for obtaining configuration information on a specific resource or in general to perform specific operations such as creating a process or reading data. The abstraction layer consists of the software deployed across the physical layer which manifests the. To be sure you have the latest version of the manual for this release go to the Yocto Project documentation page and select the manual from that site. Layer consists of the hardware resources that are necessary to support the cloud services being provided and typically includes server storage and network components.
You will find several kinds of fields in your application forms - check boxes dates data entry fields and attachments. Our professional team of writers ensures top-quality custom essay writing services. An important difference between the point-to-point datalink layers and the datalink layers used in LANs is that in a LAN each communicating device is identified by a unique datalink layer addressThis address is usually embedded in the hardware of the device and different types of. Attachments are documents that are prepared outside the application using whatever editing software you desire eg Microsoft Word converted to PDF format and then added or. This is the representation of that part of an architecture that is expressed in different diagrams. Best Customer Support Service.
Cloud computing is a model for enabling ubiquitous convenient on-demand network access to a shared pool of configurable computing resources eg networks servers storage applications and services that can be rapidly provisioned and released with minimal management effort or service provider interaction. The frameworks in this layer provide core services such as string manipulation collection management networking URL utilities contact management and preferences. Mail services directory services network resource etc are services provided by application layer. This layer mainly holds application programs to act upon the received and to be sent data. Charity Navigator partners with other organizations focused on nonprofit infrastructure and participates in a number of data collectives - this has helped foster collaboration and has reduced redundancy for nonprofits reporting data for evaluation. Our payment system is also very secure.
We will guide you on how to place your essay help. This page provides guidance on attachments. The team collects and reports data on activity in the nonprofit sector. Deep learning DL a branch of machine learning ML and artificial intelligence AI is nowadays considered as a core technology of todays Fourth Industrial Revolution 4IR or Industry 40. We do not disclose clients information to third parties. OSI Model Layer 2.
Data Representation Data representation is defined as the methods used to represent information in computers. Download PyLoris for free.
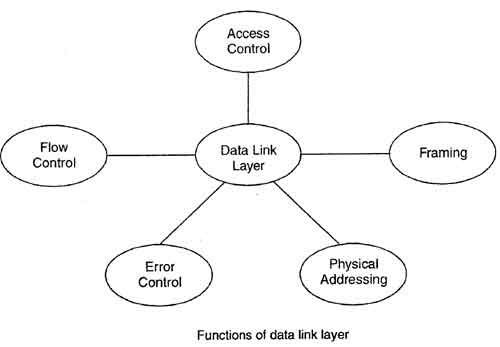
What Is Data Link Layer Definition Computer Notes
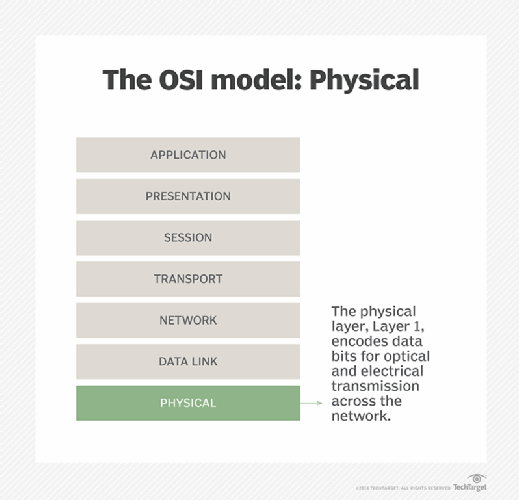
What Is Physical Layer Definition From Whatis Com
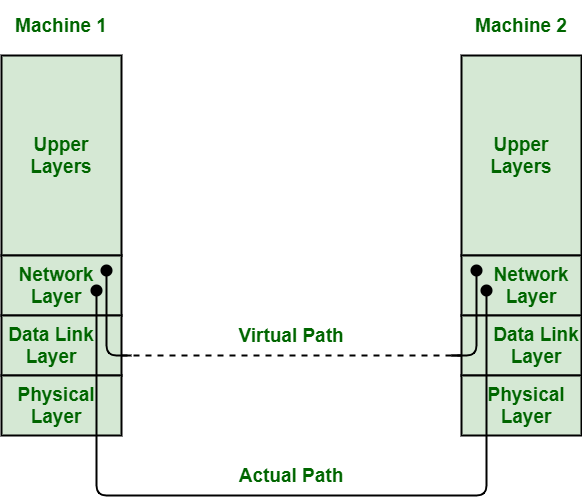
Services Provided By Data Link Layer Geeksforgeeks
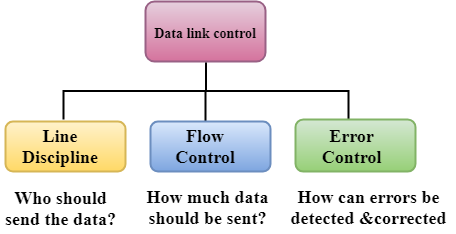
Computer Network Data Link Controls Javatpoint

Data Link Layer An Overview Sciencedirect Topics

Physical Layer Of Osi Reference Model Studytonight
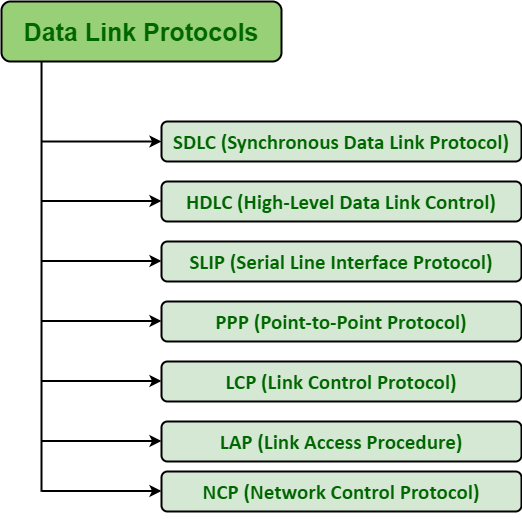
Examples Of Data Link Layer Protocols Geeksforgeeks

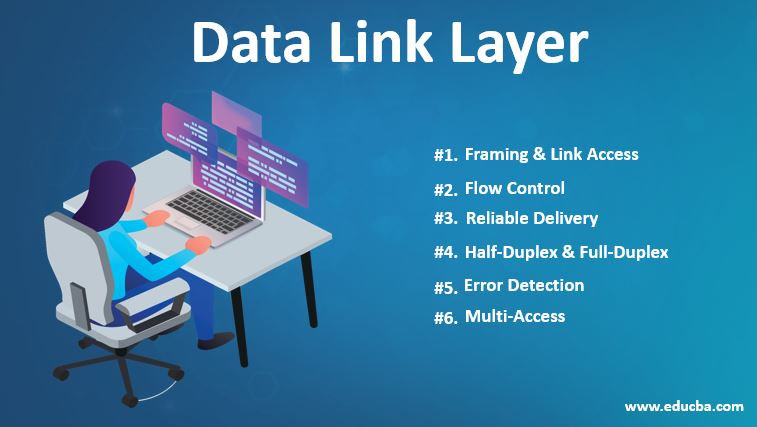
Data Link Layer Learn Top 6 Beneficial Services Of Data Link Layer

Data Link Layer An Overview Sciencedirect Topics
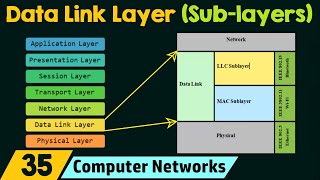
Sub Layers Of The Data Link Layer Youtube
Posting Komentar untuk "Briefly Describe The Services Provided By The Data Link Layer"